SSRF
Types of SSRF
https://website.thm/item/2?server=server.website.thm/flag?id=9&x=Finding an SSRF
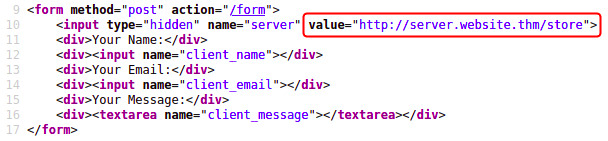
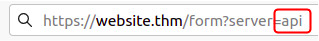
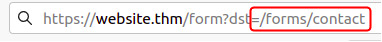
Bypass SSRF defenses
Practical

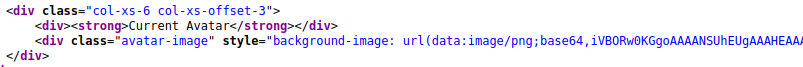
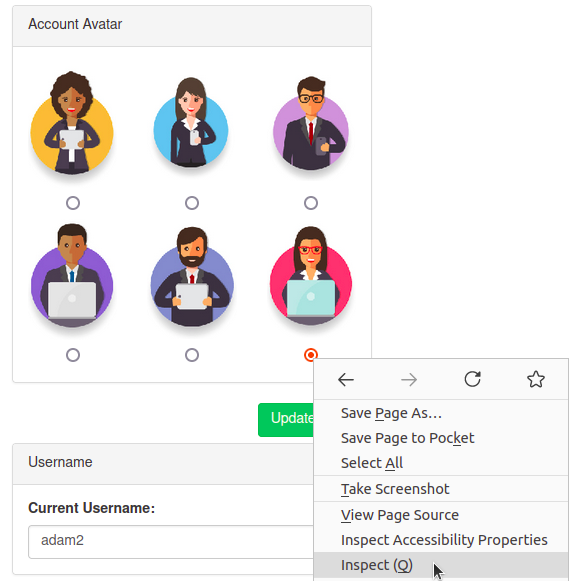
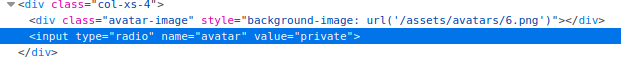
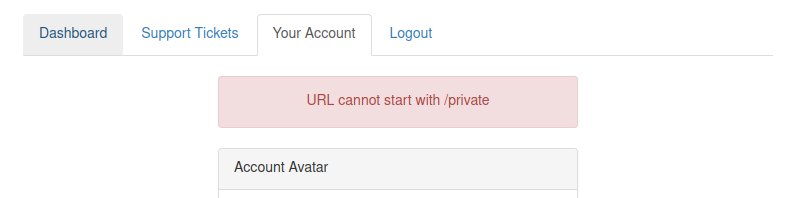
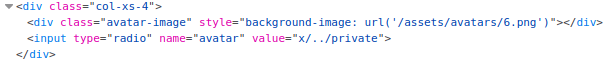
SSRF via host header
Exploit examples
SSRF via Referer header
Last updated